Security is a fundamental aspect of software development. While GitHub provides a seamless workflow for collaboration, it is equally important to ensure that every contribution is authentic, verified, and protected from malicious or accidental changes. In this guide, we will explore three key security measures: commit signing with GPG keys, branch protection rules, and enforcing security best practices.
Commit Signing with GPG Keys
What is Commit Signing?
Commit signing is a way to verify the identity of contributors in a Git repository. By signing commits with a GPG (GNU Privacy Guard) key, developers can prevent tampering and ensure that code changes originate from a trusted source.
When a commit is signed and pushed to GitHub, a ✅ Verified badge appears next to it, indicating that the commit has been authenticated.
Why is Commit Signing Important?
- Prevents commit forgery.
- Ensures accountability for each contribution.
- Adds an additional layer of security to repositories.

From https://github.blog/changelog/2022-08-23-ssh-commit-verification-now-supported/
How to Set Up GPG Commit Signing
Step 1: Install GPG
On macOS:
brew install gnupgOn Ubuntu/Debian:
sudo apt update && sudo apt install gnupgStep 2: Generate a GPG Key
gpg --full-generate-keySelect the following options:
- RSA and RSA (default)
- 4096-bit key for strong encryption
- Key expiration: Choose a suitable time frame
- Your name and email (same as your GitHub email)
Step 3: Export and Add Your Key to GitHub
gpg --list-secret-keys --keyid-format LONGCopy the GPG key ID and export it:
gpg --armor --export YOUR-KEY-IDGo to GitHub → Settings → SSH and GPG keys and add your key.
Step 4: Configure Git to Use GPG
git config --global user.signingkey YOUR-KEY-ID
git config --global commit.gpgsign trueNow, every commit you make will be signed and verified on GitHub!
Further Reading: GitHub Docs on GPG Signing
Video Guide:
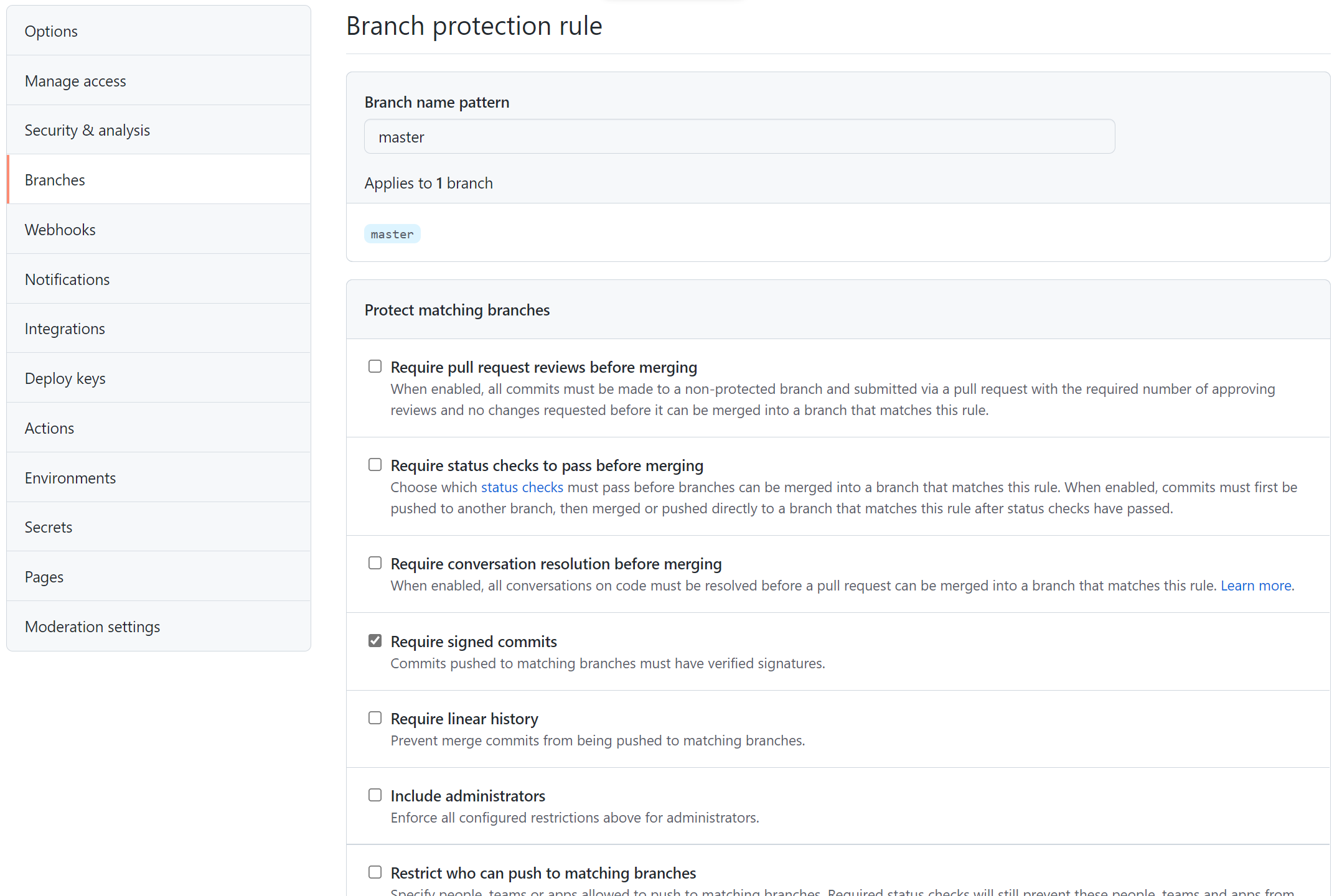
Branch Protection Rules: Keeping Your Code Secure
Why Do We Need Branch Protection?
When working in teams, mistakes happen—force-pushing to main, merging incomplete features, or skipping code reviews. Branch protection rules help prevent these issues by enforcing best practices.
Key Branch Protection Rules on GitHub
- Require Pull Requests (PRs) Before Merging
- Prevents direct pushes to
main - Ensures all changes go through review
- Prevents direct pushes to
- Require Status Checks to Pass Before Merging
- Runs automated tests (CI/CD pipelines)
- Blocks faulty code from merging
- Enforce Code Reviews
- Requires approval from team members
- Encourages collaboration and security audits
- Restrict Who Can Push to Critical Bran
- Only specific users can modify protected branches
- Prevents unauthorized changes
From https://www.cloudwithchris.com/blog/use-github-branch-protection-rules/
How to Enable Branch Protection on GitHub
- Go to your repository on GitHub.
- Navigate to Settings → Branches.
- Under Branch Protection Rules, select
main. - Enable:
- Require pull request reviews before merging.
- Require status checks to pass before merging.
- Restrict who can push to the branch.
- Click Save changes.
Further Reading: GitHub Docs on Branch Protection
Enforcing Security Best Practices in GitHub
1. Enable Two-Factor Authentication (2FA)
- Adds an extra layer of security for developers.
- Prevents unauthorized access even if passwords are compromised.
2. Use Dependabot for Automated Security Fixes
GitHub’s Dependabot scans your repository for vulnerabilities and automatically opens PRs with security patches.
- How to Enable:
- Go to Settings → Security & analysis.
- Enable Dependabot alerts and updates.

From https://i0.wp.com/user-images.githubusercontent.com/5788563/150418619-3311f32f-9127-4d7a-9b2c-c3f4609ad066.png?ssl=1
Secret Scanning & Token Protection
- GitHub automatically scans repositories for accidentally committed API keys or secrets.
- If detected, GitHub alerts the repository owner immediately.
Further Reading:
Conclusion
Security should never be an afterthought when working with GitHub. By implementing GPG commit signing, branch protection rules, and security best practices, teams can protect their repositories from malicious activity and accidental errors.
By following these steps, you ensure:
Verified, tamper-proof commits
Strict control over critical branches
Proactive security measures
Start securing your GitHub workflow today!